互聯(lián)網(wǎng)發(fā)展至今,,已由傳統(tǒng)的前后端統(tǒng)一架構(gòu)演變?yōu)槿缃竦那昂蠖朔蛛x架構(gòu),,最初的前端網(wǎng)頁大多由JSP,、ASP,、PHP等動態(tài)網(wǎng)頁技術(shù)生成,,前后端十分耦合,,也不利于擴展?,F(xiàn)在的前端分支很多,,如:Web前端、Android端,、IOS端,,甚至還有物聯(lián)網(wǎng)等。前后端分離的好處就是后端只需要實現(xiàn)一套界面,,所有前端即可通用,。
前后端的傳輸通過HTTP進行傳輸,也帶來了一些安全問題,,如果抓包,、模擬請求、洪水攻擊,、參數(shù)劫持,、網(wǎng)絡(luò)爬蟲等等。如何對非法請求進行有效攔截,,保護合法請求的權(quán)益是這篇文章需要討論的,。
作者依據(jù)多年互聯(lián)網(wǎng)后端開發(fā)經(jīng)驗,總結(jié)出了以下提升網(wǎng)絡(luò)安全的方式:
采用HTTPS協(xié)議
密鑰存儲到服務(wù)端而非客戶端,,客戶端應(yīng)從服務(wù)端動態(tài)獲取密鑰
請求隱私接口,,利用token機制校驗其合法性
對請求參數(shù)進行合法性校驗
對請求參數(shù)進行簽名認證,防止參數(shù)被篡改
對輸入輸出參數(shù)進行加密,,客戶端加密輸入?yún)?shù),,服務(wù)端加密輸出參數(shù)
那么,下面我將對以上方式展開做詳細說明,。
HTTP VS HTTPS
普通的HTTP協(xié)議是以明文形式進行傳輸,,不提供任何方式的數(shù)據(jù)加密,很容易解讀傳輸報文,。而HTTPS協(xié)議在HTTP基礎(chǔ)上加入了SSL層,,而SSL層通過證書來驗證服務(wù)器的身份,并為瀏覽器和服務(wù)器之間的通信加密,,保護了傳輸過程中的數(shù)據(jù)安全,。
動態(tài)密鑰的獲取
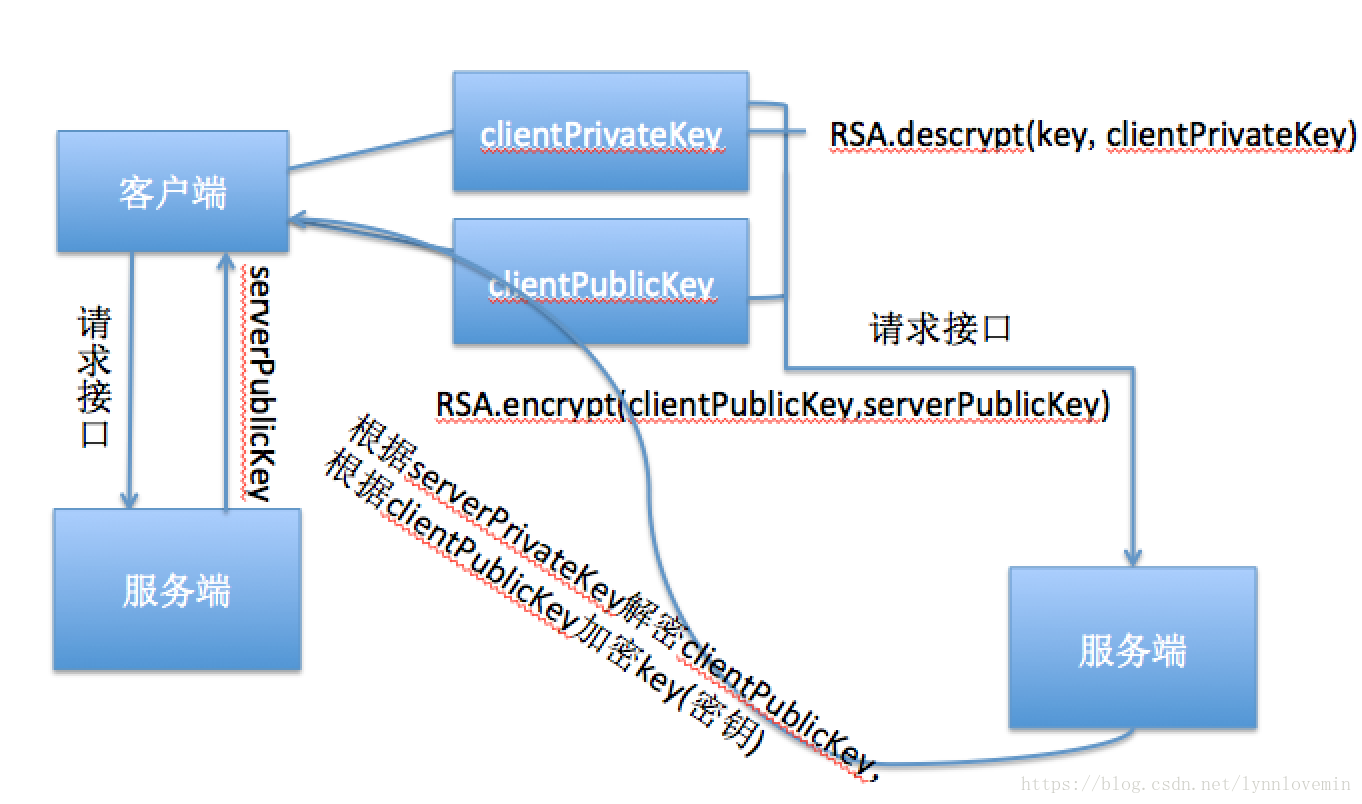
對于可逆加密算法,是需要通過密鑰進行加解密,,如果直接放到客戶端,,那么很容易反編譯后拿到密鑰,這是相當(dāng)不安全的做法,,因此考慮將密鑰放到服務(wù)端,,由服務(wù)端提供接口,讓客戶單動態(tài)獲取密鑰,,具體做法如下:
1,、客戶端先通過RSA算法生成一套客戶端的公私鑰對(clientPublicKey和clientPrivateKey)
2,、調(diào)用getRSA接口,服務(wù)端會返回serverPublicKey
3,、客戶端拿到serverPublicKey后,,用serverPublicKey作為公鑰,clientPublicKey作為明文對clientPublicKey進行RSA加密,,調(diào)用getKey接口,,將加密后的clientPublicKey傳給服務(wù)端,服務(wù)端接收到請求后會傳給客戶端RSA加密后的密鑰
4,、客戶端拿到后以clientPrivateKey為私鑰對其解密,,得到最終的密鑰,此流程結(jié)束,。
(注:上述提到的所以數(shù)據(jù)均不能保存到文件里,,必須保存到內(nèi)存中,因為只有保存到內(nèi)存中,,黑客才拿不到這些核心數(shù)據(jù),,所以每次使用獲取的密鑰前先判斷內(nèi)存中的密鑰是否存在,不存在,,則需要獲取,。)
為了便于理解,我畫了一個簡單的流程圖:
那么具體是如何實現(xiàn)的呢,,請看代碼:
#全局密鑰配置,,所以加密算法統(tǒng)一密鑰
api:
encrypt:
key: d7b85c6e414dbcda
#此配置的公司鑰信息為測試數(shù)據(jù),不能直接使用,,請自行重新生成公私鑰
rsa:
publicKey: MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCcZlkHaSN0fw3CWGgzcuPeOKPdNKHdc2nR6KLXazhhzFhe78NqMrhsyNTf3651acS2lADK3CzASzH4T0bT+GnJ77joDOP+0SqubHKwAIv850lT0QxS+deuUHg2+uHYhdhIw5NCmZ0SkNalw8igP1yS+2TEIYan3lakPBvZISqRswIDAQAB
privateKey: MIICeAIBADANBgkqhkiG9w0BAQeFAcSCAmIwggJeAgEAAoGBAJxmWQdpI3R/DcJYaDNy4944o900od1zadHootdrOGHMWF7vw2oyuGzI1N/frmxoVLaUAMrcLMBLMfhPRtP4acnvuOgM4/7RKq5scrAAi/znSVPRDFL5165QeDb64diF2EjDk0KZnRKQ1qXDyKA/XJL7ZMQhhqfeVqQ8G9khKpGzAgMBAAECgYEAj+5AkGlZj6Q9bVUez/ozahaF9tSxAbNs9xg4hDbQNHByAyxzkhALWVGZVk3rnyiEjWG3OPlW1cBdxD5w2DIMZ6oeyNPA4nehYrf42duk6AI//vd3GsdJa6Dtf2has1R+0uFrq9MRhfRunAf0w6Z9zNbiPNSd9VzKjjSvcX7OTsECQQD20kekMToC6LZaZPr1p05TLUTzXHvTcCllSeXWLsjVyn0AAME17FJRcL9VXQuSUK7PQ5Lf5+OpjrCRYsIvuZg9AkEAojdC6k3SqGnbtftLfGHMDn1fe0nTJmL05emwXgJvwToUBdytvgbTtqs0MsnuaOxMIMrBtpbhS6JiB5Idb7GArwJAfKTkmP5jFWT/8dZdBgFfhJGv6FakEjrqLMSM1QT7VzvStFWtPNYDHC2b8jfyyAkGvpSZb4ljZxUwBbuh5QgM4QJBAJDrV7+lOP62W9APqdd8M2X6gbPON3JC09EW3jaObLKupTa7eQicZsX5249IMdLQ0A43tanez3XXo0ZqNhwT8wcCQQDUubpNLwgAwN2X7kW1btQtvZW47o9CbCv+zFKJYms5WLrVpotjkrCgPeuloDAjxeHNARX8ZTVDxls6KrjLH3lT- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
<dependency>
<groupId>commons-codec</groupId>
<artifactId>commons-codec</artifactId>
</dependency>
<dependency>
<groupId>commons-io</groupId>
<artifactId>commons-io</artifactId>
<version>2.6</version>
</dependency>- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
public class AesEncryptUtils {
private static final String KEY = "d7585fde114abcda";
private static final String ALGORITHMSTR = "AES/CBC/NoPadding";
public static String base64Encode(byte[] bytes) {
return Base64.encodeBase64String(bytes);
}
public static byte[] base64Decode(String base64Code) throws Exception {
return Base64.decodeBase64(base64Code);
}
public static byte[] aesEncryptToBytes(String content, String encryptKey) throws Exception {
KeyGenerator kgen = KeyGenerator.getInstance("AES");
kgen.init(128);
Cipher cipher = Cipher.getInstance(ALGORITHMSTR);
cipher.init(Cipher.ENCRYPT_MODE, new SecretKeySpec(encryptKey.getBytes(), "AES"));
return cipher.doFinal(content.getBytes("utf-8"));
}
public static String aesEncrypt(String content, String encryptKey) throws Exception {
return base64Encode(aesEncryptToBytes(content, encryptKey));
}
public static String aesDecryptByBytes(byte[] encryptBytes, String decryptKey) throws Exception {
KeyGenerator kgen = KeyGenerator.getInstance("AES");
kgen.init(128);
Cipher cipher = Cipher.getInstance(ALGORITHMSTR);
cipher.init(Cipher.DECRYPT_MODE, new SecretKeySpec(decryptKey.getBytes(), "AES"));
byte[] decryptBytes = cipher.doFinal(encryptBytes);
return new String(decryptBytes);
}
public static String aesDecrypt(String encryptStr, String decryptKey) throws Exception {
return aesDecryptByBytes(base64Decode(encryptStr), decryptKey);
}
public static void main(String[] args) throws Exception {
String content = "{name:\"lynn\",id:1}";
System.out.println("加密前:" + content);
String encrypt = aesEncrypt(content, KEY);
System.out.println(encrypt.length() + ":加密后:" + encrypt);
String decrypt = aesDecrypt("H9pGuDMV+iJoS8YSfJ2Vx0NYN7v7YR0tMm1ze5zp0WvNEFXQPM7K0k3IDUbYr5ZIckTkTHcIX5Va/cstIPrYEK3KjfCwtOG19l82u+x6soa9FzAtdL4EW5HAFMmpVJVyG3wz/XUysIRCwvoJ20ruEwk07RB3ojc1Vtns8t4kKZE=", "d7b85f6e214abcda");
System.out.println("解密后:" + decrypt);
}
}
public class RSAUtils {
public static final String CHARSET = "UTF-8";
public static final String RSA_ALGORITHM = "RSA";
public static Map<String, String> createKeys(int keySize){
//為RSA算法創(chuàng)建一個KeyPairGenerator對象
KeyPairGenerator kpg;
try{
kpg = KeyPairGenerator.getInstance(RSA_ALGORITHM);
}catch(NoSuchAlgorithmException e){
throw new IllegalArgumentException("No such algorithm-->[" + RSA_ALGORITHM + "]");
}
//初始化KeyPairGenerator對象,密鑰長度
kpg.initialize(keySize);
//生成密匙對
KeyPair keyPair = kpg.generateKeyPair();
//得到公鑰
Key publicKey = keyPair.getPublic();
String publicKeyStr = Base64.encodeBase64String(publicKey.getEncoded());
//得到私鑰
Key privateKey = keyPair.getPrivate();
String privateKeyStr = Base64.encodeBase64String(privateKey.getEncoded());
Map<String, String> keyPairMap = new HashMap<>(2);
keyPairMap.put("publicKey", publicKeyStr);
keyPairMap.put("privateKey", privateKeyStr);
return keyPairMap;
}
/**
* 得到公鑰
* @param publicKey 密鑰字符串(經(jīng)過base64編碼)
* @throws Exception
*/
public static RSAPublicKey getPublicKey(String publicKey) throws NoSuchAlgorithmException, InvalidKeySpecException {
//通過X509編碼的Key指令獲得公鑰對象
KeyFactory keyFactory = KeyFactory.getInstance(RSA_ALGORITHM);
X509EncodedKeySpec x509KeySpec = new X509EncodedKeySpec(Base64.decodeBase64(publicKey));
RSAPublicKey key = (RSAPublicKey) keyFactory.generatePublic(x509KeySpec);
return key;
}
/**
* 得到私鑰
* @param privateKey 密鑰字符串(經(jīng)過base64編碼)
* @throws Exception
*/
public static RSAPrivateKey getPrivateKey(String privateKey) throws NoSuchAlgorithmException, InvalidKeySpecException {
//通過PKCS#8編碼的Key指令獲得私鑰對象
KeyFactory keyFactory = KeyFactory.getInstance(RSA_ALGORITHM);
PKCS8EncodedKeySpec pkcs8KeySpec = new PKCS8EncodedKeySpec(Base64.decodeBase64(privateKey));
RSAPrivateKey key = (RSAPrivateKey) keyFactory.generatePrivate(pkcs8KeySpec);
return key;
}
/**
* 公鑰加密
* @param data
* @param publicKey
* @return
*/
public static String publicEncrypt(String data, RSAPublicKey publicKey){
try{
Cipher cipher = Cipher.getInstance(RSA_ALGORITHM);
cipher.init(Cipher.ENCRYPT_MODE, publicKey);
return Base64.encodeBase64String(rsaSplitCodec(cipher, Cipher.ENCRYPT_MODE, data.getBytes(CHARSET), publicKey.getModulus().bitLength()));
}catch(Exception e){
throw new RuntimeException("加密字符串[" + data + "]時遇到異常", e);
}
}
/**
* 私鑰解密
* @param data
* @param privateKey
* @return
*/
public static String privateDecrypt(String data, RSAPrivateKey privateKey){
try{
Cipher cipher = Cipher.getInstance(RSA_ALGORITHM);
cipher.init(Cipher.DECRYPT_MODE, privateKey);
return new String(rsaSplitCodec(cipher, Cipher.DECRYPT_MODE, Base64.decodeBase64(data), privateKey.getModulus().bitLength()), CHARSET);
}catch(Exception e){
throw new RuntimeException("解密字符串[" + data + "]時遇到異常", e);
}
}
/**
* 私鑰加密
* @param data
* @param privateKey
* @return
*/
public static String privateEncrypt(String data, RSAPrivateKey privateKey){
try{
Cipher cipher = Cipher.getInstance(RSA_ALGORITHM);
cipher.init(Cipher.ENCRYPT_MODE, privateKey);
return Base64.encodeBase64String(rsaSplitCodec(cipher, Cipher.ENCRYPT_MODE, data.getBytes(CHARSET), privateKey.getModulus().bitLength()));
}catch(Exception e){
throw new RuntimeException("加密字符串[" + data + "]時遇到異常", e);
}
}
/**
* 公鑰解密
* @param data
* @param publicKey
* @return
*/
public static String publicDecrypt(String data, RSAPublicKey publicKey){
try{
Cipher cipher = Cipher.getInstance(RSA_ALGORITHM);
cipher.init(Cipher.DECRYPT_MODE, publicKey);
return new String(rsaSplitCodec(cipher, Cipher.DECRYPT_MODE, Base64.decodeBase64(data), publicKey.getModulus().bitLength()), CHARSET);
}catch(Exception e){
throw new RuntimeException("解密字符串[" + data + "]時遇到異常", e);
}
}
private static byte[] rsaSplitCodec(Cipher cipher, int opmode, byte[] datas, int keySize){
int maxBlock = 0;
if(opmode == Cipher.DECRYPT_MODE){
maxBlock = keySize / 8;
}else{
maxBlock = keySize / 8 - 11;
}
ByteArrayOutputStream out = new ByteArrayOutputStream();
int offSet = 0;
byte[] buff;
int i = 0;
try{
while(datas.length > offSet){
if(datas.length-offSet > maxBlock){
buff = cipher.doFinal(datas, offSet, maxBlock);
}else{
buff = cipher.doFinal(datas, offSet, datas.length-offSet);
}
out.write(buff, 0, buff.length);
i++;
offSet = i * maxBlock;
}
}catch(Exception e){
throw new RuntimeException("加解密閥值為["+maxBlock+"]的數(shù)據(jù)時發(fā)生異常", e);
}
byte[] resultDatas = out.toByteArray();
IOUtils.closeQuietly(out);
return resultDatas;
}
public static void main(String[] args) throws Exception{
Map<String, String> keyMap = RSAUtils.createKeys(1024);
String publicKey = keyMap.get("publicKey");
String privateKey = "MIICeAIBADANBgkqhkiG9w0BAQEFAASCAmIwggJeAgEAAoGBAJxmWQdpI3R/DcJYaDNy4944o900od1zadHootdrOGHMWF7vw2oyuGzI1N/frmxoVLaUAMrcLMBLMfhPRtP4acnvuOgM4/7RKq5scrAAi/znSVPRDFL5165QeDb64diF2EjDk0KZnRKQ1qXDyKA/XJL7ZMQhhqfeVqQ8G9khKpGzAgMBAAECgYEAj+5AkGlZj6Q9bVUez/ozahaF9tSxAbNs9xg4hDbQNHByAyxzkhALWVGZVk3rnyiEjWG3OPlW1cBdxD5w2DIMZ6oeyNPA4nehYrf42duk6AI//vd3GsdJa6Dtf2has1R+0uFrq9MRhfRunAf0w6Z9zNbiPNSd9VzKjjSvcX7OTsECQQD20kekMToC6LZaZPr1p05TLUTzXHvTcCllSeXWLsjVyn0AAME17FJRcL9VXQuSUK7PQ5Lf5+OpjrCRYsIvuZg9AkEAojdC6k3SqGnbtftLfGHMDn1fe0nTJmL05emwXgJvwToUBdytvgbTtqs0MsnuaOxMIMrBtpbhS6JiB5Idb7GArwJAfKTkmP5jFWT/8dZdBgFfhJGv6FYkEjrqLMSM1QT7VzvStFWtPNYDHC2b8jfyyAkGvpSZb4ljZxUwBbuh5QgM4QJBAJDrV7+lOP62W9APqdd8M2X6gbPON3JC09EW3jaObLKupTa7eQicZsX5249IMdLQ0A43tanez3XXo0ZqNhwT8wcCQQDUubpNLwgAwN2X7kW1btQtvZW47o9CbCv+zFKJYms5WLrVpotjkrCgPeuloDAjxeHNARX8ZTVDxls6KrjLH3lT";
System.out.println("公鑰: \n\r" + publicKey);
System.out.println("私鑰: \n\r" + privateKey);
System.out.println("公鑰加密——私鑰解密");
String str = "站在大明門前守衛(wèi)的禁衛(wèi)軍,,事先沒有接到\n" +
"有關(guān)的命令,但看到大批盛裝的官員來臨,,也就\n" +
"以為確系舉行大典,,因而未加詢問,。進大明門即\n" +
"為皇城,。文武百官看到端門午門之前氣氛平靜,\n" +
"城樓上下也無朝會的跡象,,既無幾案,,站隊點名\n" +
"的御史和御前侍衛(wèi)“大漢將軍”也不見蹤影,不免\n" +
"心中揣測,,互相詢問:所謂午朝是否訛傳,?";
System.out.println("\r明文:\r\n" + str);
System.out.println("\r明文大小:\r\n" + str.getBytes().length);
String encodedData = RSAUtils.publicEncrypt(str, RSAUtils.getPublicKey(publicKey));
System.out.println("密文:\r\n" + encodedData);
String decodedData = RSAUtils.privateDecrypt("X4hHPa9NjPd5QJGPus+4+hWmOzbWg7oCJ1+Vc+7dHW81nEhkYnJpFyV5xcDkg70N2Mym+YAJ1PvYY9sQWf9/EkUE61TpUKBmDaGWLjEr3A1f9cKIelqLKLsJGdXEOr7Z55k4vYFvA7N3Vf5KQo3NrouvIT4wR+SjH4tDQ8tNh3JH8BvXLtXqGa2TCK2z1AzHNgYzcLCrqDasd7UDHRPZPiW4thktM/whjBn0tU9B/kKjAjLuYttKLEmy5nT7v7u16aZ6ehkk+kzvuCXF%2B3RsqraISDPbsTki2agJyqsycRx3w7CvKRyUbZhFaNcWigOwmcbZVoiom+ldh7Vh6HYqDA==", RSAUtils.getPrivateKey(privateKey));
System.out.println("解密后文字: \r\n" + decodedData);
}
}
/**
* 私鑰輸入?yún)?shù)(其實就是客戶端通過服務(wù)端返回的公鑰加密后的客戶端自己生成的公鑰)
*/
public class KeyRequest {
/**
* 客戶端自己生成的加密后公鑰
*/
@NotNull
private String clientEncryptPublicKey;
public String getClientEncryptPublicKey() {
return clientEncryptPublicKey;
}
public void setClientEncryptPublicKey(String clientEncryptPublicKey) {
this.clientEncryptPublicKey = clientEncryptPublicKey;
}
}
/**
* RSA生成的公私鑰輸出參數(shù)
*/
public class RSAResponse extends BaseResponse{
private String serverPublicKey;
private String serverPrivateKey;
public static class Builder{
private String serverPublicKey;
private String serverPrivateKey;
public Builder setServerPublicKey(String serverPublicKey){
this.serverPublicKey = serverPublicKey;
return this;
}
public Builder setServerPrivateKey(String serverPrivateKey){
this.serverPrivateKey = serverPrivateKey;
return this;
}
public RSAResponse build(){
return new RSAResponse(this);
}
}
public static Builder options(){
return new Builder();
}
public RSAResponse(Builder builder){
this.serverPrivateKey = builder.serverPrivateKey;
this.serverPublicKey = builder.serverPublicKey;
}
public String getServerPrivateKey() {
return serverPrivateKey;
}
public String getServerPublicKey() {
return serverPublicKey;
}
}
/**
* 私鑰輸出參數(shù)
*/
public class KeyResponse extends BaseResponse{
/**
* 整個系統(tǒng)所有加密算法共用的密鑰
*/
private String key;
public static class Builder{
private String key;
public Builder setKey(String key){
this.key = key;
return this;
}
public KeyResponse build(){
return new KeyResponse(this);
}
}
public static Builder options(){
return new Builder();
}
private KeyResponse(Builder builder){
this.key = builder.key;
}
public String getKey() {
return key;
}
}
/**
* API傳輸加解密相關(guān)接口
*/
public interface EncryptOpenService {
/**
* 生成RSA公私鑰
* @return
*/
SingleResult<RSAResponse> getRSA();
/**
* 獲得加解密用的密鑰
* @param request
* @return
*/
SingleResult<KeyResponse> getKey(KeyRequest request) throws Exception;
}- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
- 309
- 310
- 311
- 312
- 313
- 314
- 315
- 316
- 317
- 318
- 319
- 320
- 321
- 322
- 323
- 324
- 325
- 326
- 327
- 328
- 329
- 330
- 331
- 332
- 333
- 334
- 335
- 336
- 337
- 338
- 339
- 340
- 341
- 342
- 343
- 344
- 345
- 346
- 347
- 348
@Service
public class EncryptOpenServiceImpl implements EncryptOpenService{
@Value("${rsa.publicKey}")
private String publicKey;
@Value("${rsa.privateKey}")
private String privateKey;
@Value("${api.encrypt.key}")
private String key;
@Override
public SingleResult<RSAResponse> getRSA() {
RSAResponse response = RSAResponse.options()
.setServerPublicKey(publicKey)
.build();
return SingleResult.buildSuccess(response);
}
@Override
public SingleResult<KeyResponse> getKey(KeyRequest request)throws Exception {
String clientPublicKey = RSAUtils.privateDecrypt(request.getClientEncryptPublicKey(), RSAUtils.getPrivateKey(privateKey));
String encryptKey = RSAUtils.publicEncrypt(key,RSAUtils.getPublicKey(clientPublicKey));
KeyResponse response = KeyResponse.options()
.setKey(encryptKey)
.build();
return SingleResult.buildSuccess(response);
}
}
@RestController
@RequestMapping("open/encrypt")
public class EncryptController {
@Autowired
private EncryptOpenService encryptOpenService;
@RequestMapping(value = "getRSA",method = RequestMethod.POST)
//@DisabledEncrypt
public SingleResult<RSAResponse> getRSA(){
return encryptOpenService.getRSA();
}
@RequestMapping(value = "getKey",method = RequestMethod.POST)
//@DisabledEncrypt
public SingleResult<KeyResponse> getKey(@Valid @RequestBody KeyRequest request)throws Exception{
return encryptOpenService.getKey(request);
}
}- 1